
As you probably know, the Trump administration banned US companies from doing business with Huawei several months ago. Recently Huawei had a big smartphone launch, the Mate 30 Pro, the first Huawei phone to launch without Google apps, thanks to the export ban. The lack of Google apps is a serious black mark on the device, as it is now shipping without the Android app ecosystem and without killer Google apps like the Play Store, Gmail, Google Maps, YouTube, Chrome, the Google Assistant, and more.
The Internet, as it is wont to do, has been coming up with workarounds to fix this problem to get Google apps on the Mate 30 Pro. The gray market distribution of Google apps is something the Android modding scene has down to a science, and it’s fairly easy to get Google apps on things that don’t normally come with Google apps, like Amazon Kindle Fire devices, custom ROMs based on the open source Android code (like LineageOS), and on imported devices meant for the Google-free Chinese market.
Unfortunately, none of these methods works on the Mate 30 Pro. They rely on either an unlocked bootloader, which allows users to flash Google apps to the normally read-only system partition, or they rely on “stub apps” left in the system partition by the device manufacturer specifically for the Google apps, so sideloaded versions can get the system-level permissions they need to work. The Mate 30 doesn’t allow for either method.
With all the traditional techniques out the window, the Internet’s brand-new method for getting Google apps onto the Mate 30 is through a website called Lzplay.net. You can see news articles promoting this site from just about all the major Android news sites. I Googled “mate 30 pro install play store,” and literally every result on the first page recommended Lzplay.net. It’s easy to see why Lzplay is ubiquitous: go to the website, install the app, mash “next” a few times, and boom, Google apps are on your Huawei device.
It seemingly installs six system apps in the blink of an eye with almost no user interaction. Even though the Google apps should not be able to get the system-level permissions they need to work, they somehow do, thanks to this app. It’s like magic.
Lzplay is fast, it’s easy, and as far as getting Google apps onto your Huawei device, it works. It’s also the biggest Android modding security nightmare I have ever seen. And no, that’s not hyperbole.
Protip: Don’t set a random Chinese website as the remote administrator of your smartphone
Lzplay.net plugs into Android’s Mobile Device Management (MDM) API, which is meant for enterprise services like Android for Work, or your company’s IT department. This is a remote management API that is meant to give your IT department full control over a company-issued device. The goal is to allow your IT department to have, basically, as much control over the device remotely as you have in front of it, allowing them to silently install and uninstall apps, change the lock screen password, remote-wipe the device, and do a million other things.
Watch any of the video guides after the app is download and you’ll see the “Activate device administrator?” screen pop up, complete with the huge, scrolling list that spells out all the scary permissions. At this point you should really stop and think if granting these permissions to an unknown entity is a good idea. (It’s totally not.)
This set of permissions, which used to be called “Device owner,” should only ever be given to an entity you 100-percent trust: Apps like Google’s Android for Work, an app from your company’s MDM provider for your company-issued phone, or maybe you have an Android-powered kiosk or IoT device that you personally want to manage remotely. Those options are fine. What’s not fine is granting these permissions to a random website like Lzplay.net.
Nobody knows who or what owns Lzplay.net, and therefore nobody knows if the site is trustworthy or what they want out of all this. With no copyright notice or any kind of ownership claim on the website, there’s not much digging that can be done. A whois lookup shows the site is hosted in mainland China and was created just three months ago, and neither of those facts inspires much confidence.
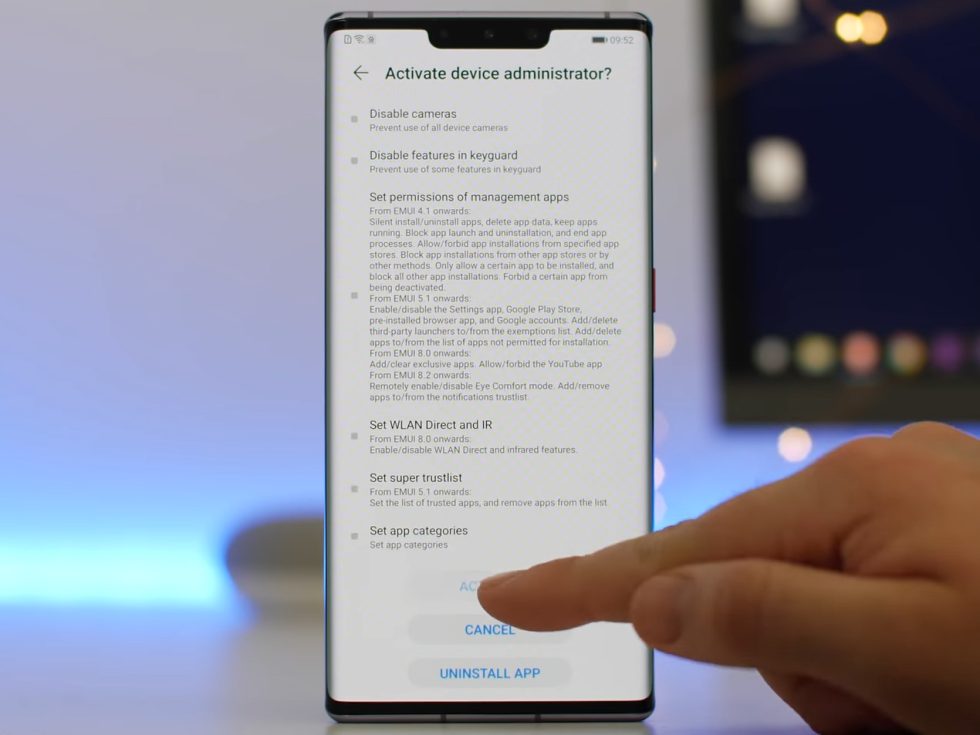
A lot of the write-ups and videos out there gloss over how Lzplay works and just how many permissions it has access to. You visit the website, install the Lzplay app, and then grant it the ultra-powerful device administrator permissions, at which point it does its thing and installs the Google apps. At this point most of the guides go on to talk about how you are pretty much done and how you might have to reset your device afterward. Almost none of them mentions how you still have this Lzplay.net app set as your device’s administrator, and how, unless you uninstall it, you have this random third party with a backdoor to your phone, forever. Uninstalling the device administrator app is not as easy as uninstalling a normal app, either—you can’t remove the app unless you first dig through the settings and remove it as the administrator first.
The Android modding scene has always had some issues with security. Modding often involves encouraging people to install apps with powerful root permissions that could do very nasty, malicious things to a phone if they wanted. The way the community usually works around this is by either installing apps that are open source, where anyone can audit the code and see what it is doing, or by using a handful of trusted root app developers that have been around for years and years and have proven themselves to the community. In the case of installing Google apps, the normal Google app distributors like Open Gapps have you flash a one-time package to your system partition and you’re done. The scripts to do this are open source, and you can verify the proprietary Google applications it installs haven’t been tampered with, thanks to Android’s APK signing.
The Lzplay.net method doesn’t get any of these community safety nets. As I mentioned before, the site is three months old, hosted in China, and no one knows who owns it. What is really egregious, though, is this whole remote backdoor situation, assuming you leave Lzplay on your phone, like most of the guides suggest. Lzplay might not do anything malicious today, but since it still has device administrator privileges, tomorrow it could easily fill your phone with bitcoin miners, remotely install ransomware, or brick your phone. I don’t recommend using this method at all, and leaving this grossly powerful app around on your phone, forever, is a huge security problem.























