
The new Windows CryptoAPI CVE-2020-0601 vulnerability disclosed by the NSA can be abused by malware developers to sign their executables so that they appear to be from legitimate companies. This creates trust in the program, which may cause a user to be more willing to execute them.
Most of the coverage of this vulnerability illustrates how the vulnerability can be exploited to spoof certificates used for TLS connections to web sites and perform MiTM attacks.
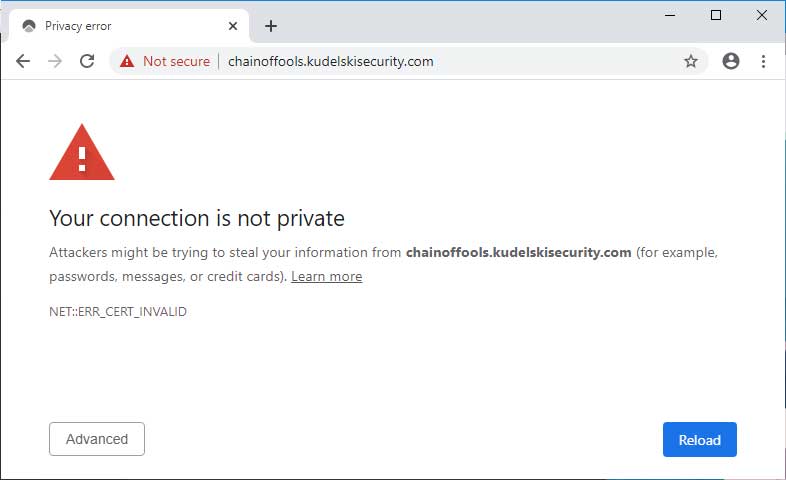
For example, Kudelski Security illustrated how they used the vulnerability to create a fake certificate that impersonates github.com. To protect users, Chrome added protections that block users from accessing sites using these spoofed certificates.
This vulnerability, though, can also be used to spoof code-signing certificates.
When a developer releases a program, they can digitally sign the executables to assure users that the program is from a trusted source. If that user trusts the company, then their signed executables are most likely trustworthy as well and would be more apt to execute them.
Antivirus software may also whitelist software from being detected as malware if they utilize trusted and well-known digital signatures.
Using this new CryptoAPI vulnerability, malware distributors can create code-signing certificates that spoof legitimate companies so that their signed malware executables appear to be from a trusted company like Microsoft.
It’s about trust
When running an executable in Windows that requires elevated, or administrative, privileges the operating system will display a User Account Control (UAC) prompt asking you to confirm if the permission should be granted.
If the executable has been code-signed, the UAC prompt will display a blue banner, the product name of the executable, its icon, and the name of the developer listed in the code-signing certificate. The user can then use this information to decide if they should grant elevated privileges to the program.
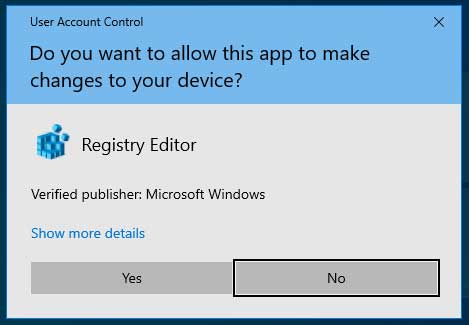
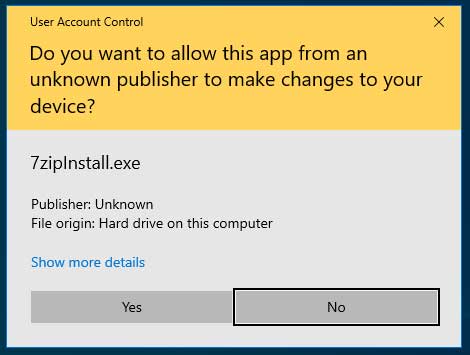
When this same executable is unsigned, Windows will display a UAC prompt with a yellow banner that specifies the publisher is ‘Unknown’ and once again asking if you would like to give elevated privileges.
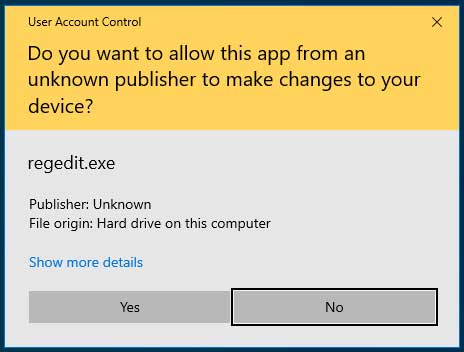
As you can see from the two prompts above, the one for the unsigned executable is intended to make the user more wary about providing administrative privileges.
Due to this, malware distributors are commonly creating fake companies to purchase code-signing certificates or stealing certificates from other companies. These certificates are then used to sign their malware executables.
The problem for attackers, though, is that once a certificate is reported to be used with malware, the certificate authority responsible for this cert will revoke it so that it no longer works.
Using CVE-2020-0601 to spoof trusted publishers
Using the CVE-2020-0601 vulnerability, malware distributors can easily create certificates that spoof legitimate companies such as Microsoft.
This allows them to sign their executables so that they appear as the same code signing certificate as seen in Windows executables. Even worse, as these certificates are exploiting a vulnerability, they cannot be revoked by certificate authorities or blocked on unpatched Windows devices.
By signing an executable as a trusted publisher, it could also allow malware to bypass antivirus engines that have whitelisted the trusted certificate.
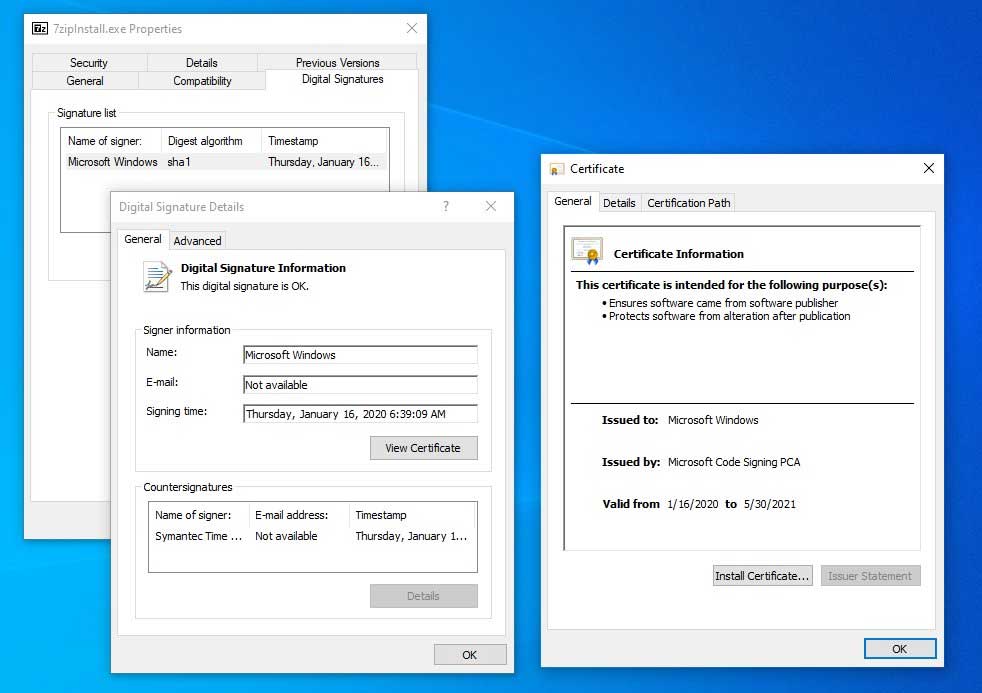
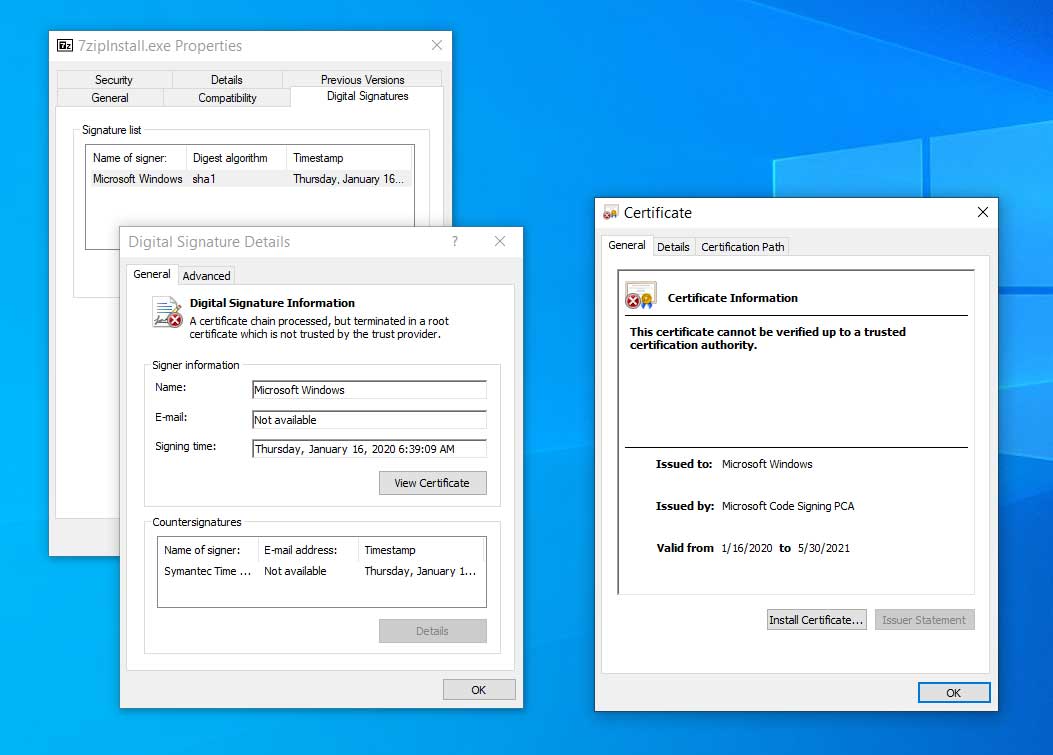
To illustrate this, BleepingComputer found an executable on VirusTotal that is signed with a certificate exploiting the CVE-2020-0601 vulnerability. This certificate spoofs the ones used by Microsoft to sign Windows executables.
On an unpatched system, Windows does not see anything wrong with the certificate when it is opened.
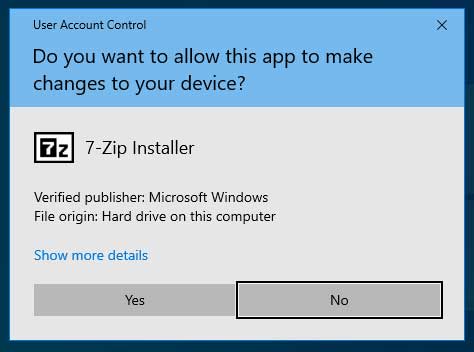
Even when you run the program, it displays a UAC prompt indicating it was signed by Microsoft.
On a patched system, though, Windows will see that this certificate is spoofed and display a warning stating “A certificate chain processed, but terminated in a root certificate which is not trusted by the trust provider.”
UAC prompts on a patched system will also ignore the spoofed certificate and treat the application as untrusted.
It is not a question as to whether malware will exploit this vulnerability, but a question as to when.
Already on VirusTotal, we see researchers uploading executables signed with spoofed certificates and can expect to see malware using it in the wild soon.
With easy to use proof-of-concepts available, this vulnerability allows attackers to generate signed malware that looks trusted and possibly bypass antivirus software.
Even better, it allows them to do so without the cost or hardship of acquiring a legitimate code-signing certificate that can easily be revoked.
“This is an immediate high-impact scenario for malware bypass. For the past year, malware deliveries have reused a signed malware to bypass AV systems relying on this check rather than their own. At its best, the criminals would leverage this vulnerability against unpatched Windows 10 as part of “free” malware signing bypassing static and/or trust-based detection,” Head of SentinelLabs Vitali Kremez told BleepingComputer in a conversation about this vulnerability.
Windows Defender detects malicious certificates
The good news is that antivirus software, web browsers, and Microsoft have been hard at work implementing detections for these spoofed certificates.
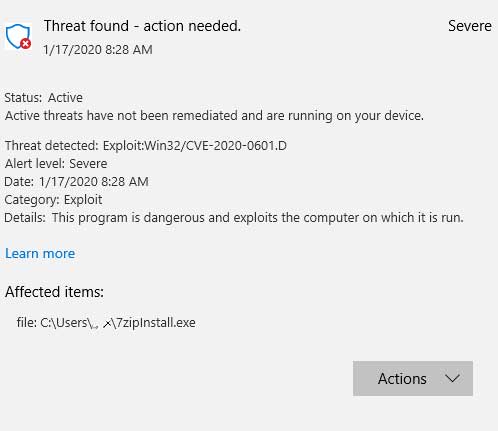
Windows Defender will now detect programs signed with certificates that exploit this vulnerability as Exploit:Win32/CVE-2020-0601.
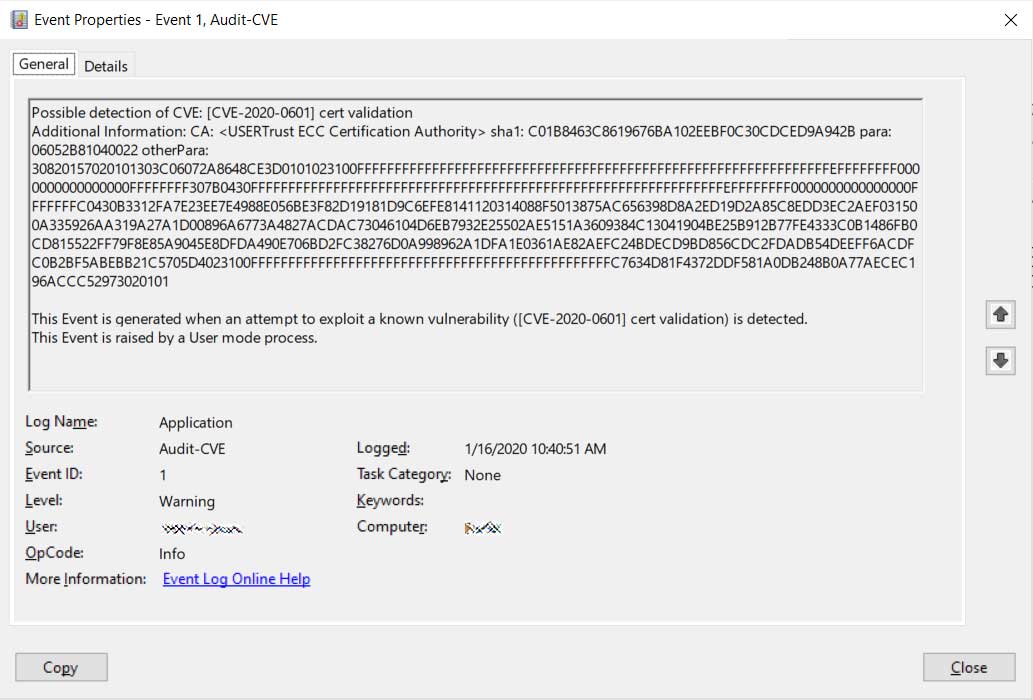
Microsoft is also utilizing the CveEventWrite function to log attempts to exploit the CVE-2020-0601 vulnerability to the Event Viewer.
Google Chrome added new protections in Chrome 79.0.3945.130 that prevent you from accessing sites using spoofed certificates.
Finally, antivirus engines such as ones from McAfee, Kaspersky, ZoneAlarm, and GData have added detections for this vulnerability and others will do the same.Paragraph
If so many security companies and software developers are taking this vulnerability seriously, so should you.
Be sure to install the patch as soon as possible to become protected.
























